Joshua Powers
on 15 October 2020
Introducing Ubuntu support for Amazon EKS 1.18
This article originally appeared on the Amazon AWS Blog.
Amazon Elastic Kubernetes Service (EKS) is a fully automated Kubernetes cluster service on Amazon Web Services (AWS). Ubuntu is a popular and proven operating system for both virtual machine and containerized cloud computing. Canonical (the creator and primary maintainer of Ubuntu) is an Amazon partner and works with the EKS team to provide an optimized Ubuntu Amazon Machine Image (AMI) for running Kubernetes on AWS. EKS-optimized Ubuntu AMIs give you the familiarity and consistency of using Ubuntu, optimized for performance and security on EKS clusters.
Ubuntu optimized AMIs for Amazon EKS and Kubernetes versions 1.17 and 1.18 are now available. These images combine the Ubuntu OS with Canonical’s distribution of upstream Kubernetes that automates K8s deployment and operations. In addition to using a slimmed-down, minimal image these images take advantage of a custom kernel that is jointly developed with AWS.
You can find the EKS-optimized Ubuntu AMI IDs for a variety of AWS regions on the Ubuntu Cloud Images EKS site.
Running Ubuntu Managed Node Groups
Amazon EKS recently announced support for launch template and custom AMI support for EKS managed node groups. This feature lets you leverage the simplicity of managed node provisioning and lifecycle management features while allowing for any level of customization, compliance, or security requirements. Previously, using Ubuntu with EKS required provisioning and managing your own EC2 instances. Now you can use managed node groups with a custom Ubuntu AMI to provide compute for your Amazon EKS cluster.
To use Ubuntu with EKS, we will first create an EKS cluster and an Amazon EC2 launch template. EC2 launch templates enable users to create versioned, declarative instance configuration specifications that meet their specific needs. For example, the launch template can specify instance types, custom AMI ID, tags, networking, as well as other configuration options. Next, we will create a managed node group using the launch template and start our nodes.
Let’s get started! The rest of this post will take you through the process of launching a managed node group with a launch template using an Ubuntu EKS AMI.
Prerequisites
We assume that you already have a running EKS cluster. If not, you can start a new cluster following the instructions in the EKS documentation. Since the focus of this post is to start Ubuntu nodes for your cluster, you don’t need to provision any nodes for your cluster yet.
While your cluster is starting, create a node IAM role with the following IAM policies:
Create an EC2 Launch Template
The first step is to create the EC2 Launch Template. The launch template is very flexible and allows for a number of customizations. You can learn more about customizing a launch template for your managed node group in the EKS documentation. Because launch templates are versioned, you can update these parameters at any time and deploy those updates across your node group

To create a launch template using an EKS-optimized Ubuntu AMI, enter the following parameters:
- Amazon machine image (AMI): Enter in one of the Ubuntu optimized EKS AMI IDs. The latest AMI IDs are published at https://cloud-images.ubuntu.com/docs/aws/eks
- Instance type: Choose the EC2 instance type for your node group. You must choose the instance type for the node group during template creation.
- Key pair (login): The key pair enables you to SSH directly into the instance after it starts. This is optional, but must be entered as part of the launch template.
- Security groups: Under Network settings, choose the security group required for the cluster. Be default users should use the security group created by the EKS cluster (e.g. named “eks-cluster-sg-*”)
- User data: Under Advanced details, at the bottom, is a section for user data. With EKS nodes, user data is passed to the instance to connect the node to the cluster. Add the following and replace the cluster name with your EKS cluster name:
#!/bin/bash
/etc/eks/bootstrap.sh {cluster name}Again, these are the minimum items that users need to consider. You can further customize the template based on your needs. Be aware that some settings like IAM instance profile and spot instances are not configurable. For a full list with more details, see the documentation on the launch template support page.
Launch a Node Group with Template
With our launch template defined, we can use EKS to start the EC2 instances for the cluster. Go to the EKS cluster and under the Compute tab click “Add Node Group”. On the new page, enable the “Use launch template” option and choose the template name created above
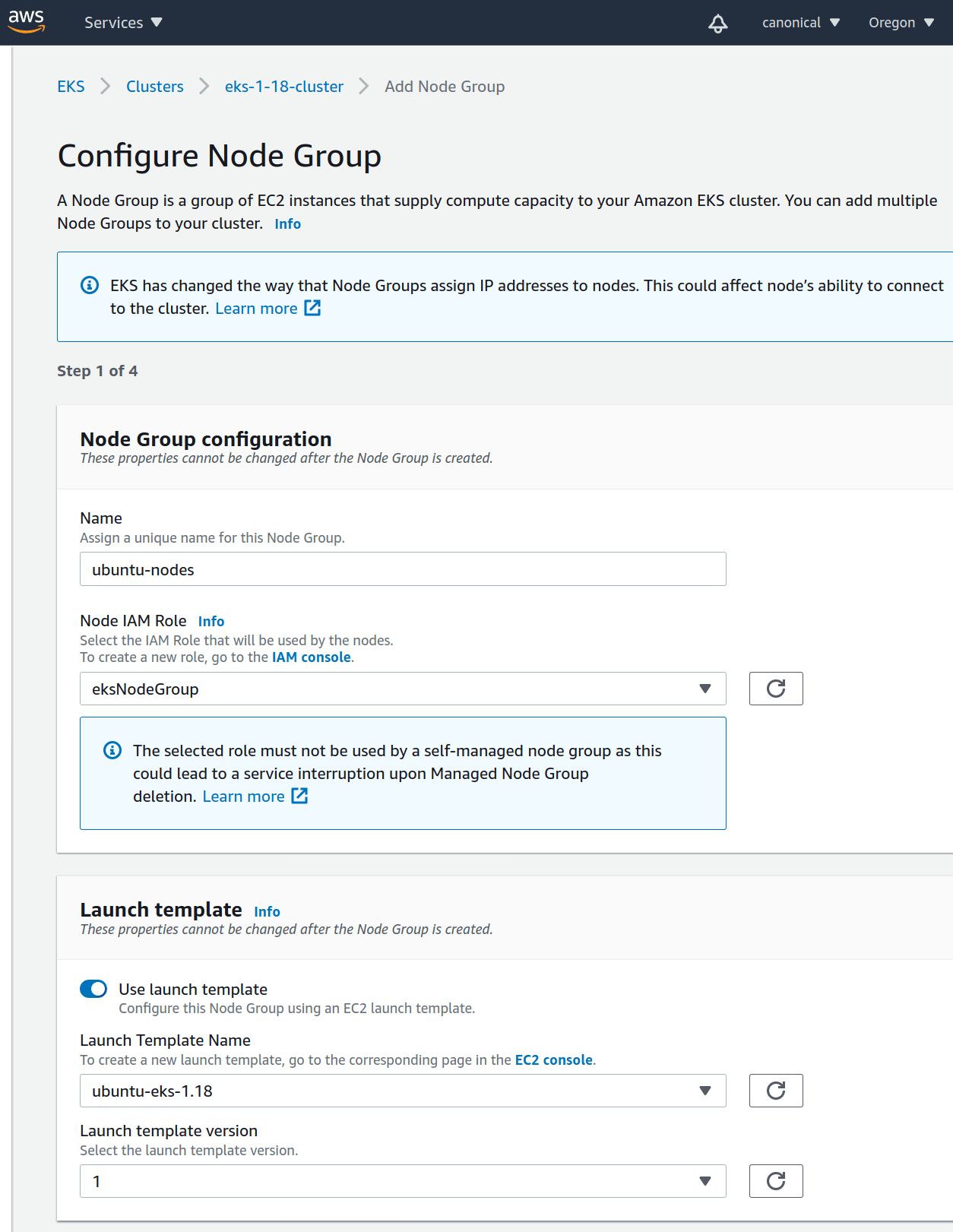
Continue through the setup process and create the node group.
In the AWS Console, the status will show up as Active once the nodes are launched and connected to the cluster:
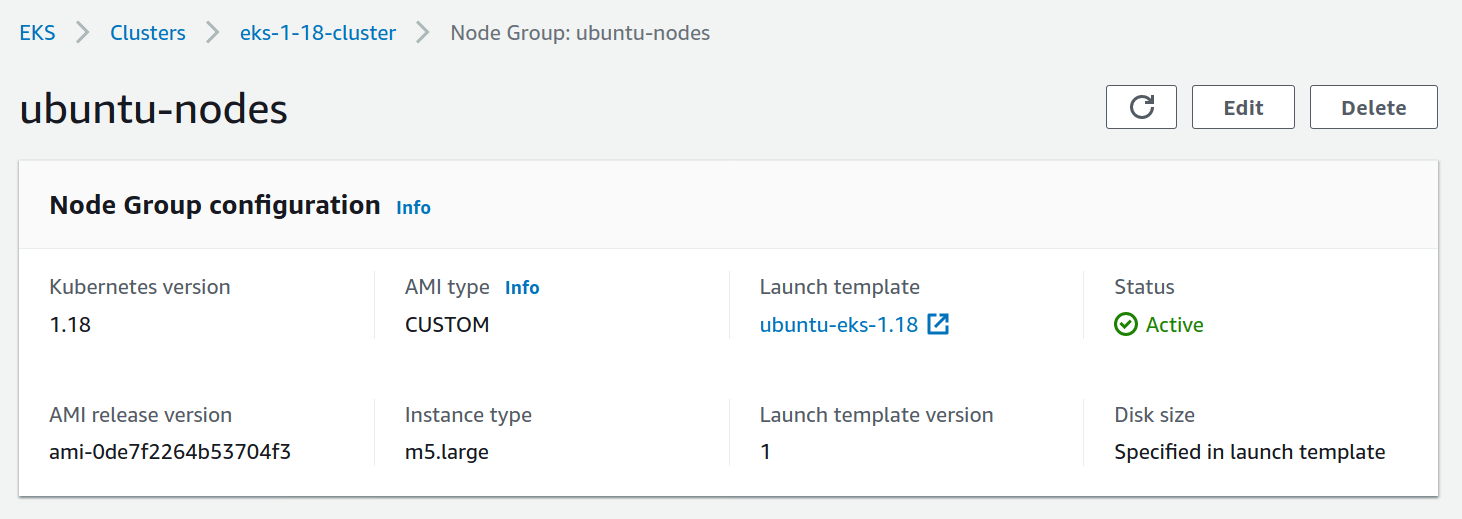
Using the AWS CLI
We just walked through using the AWS console to create your Ubuntu node group. You can do these same steps using the AWS CLI.
First, capture the launch template data as JSON. This includes the user data that will get passed to the instance into base64. Below is an example, only specifying the minimum required items
{
"LaunchTemplateData": {
"ImageId": "ami-018a7f43b2beb7a00",
"InstanceType": "m5.large",
"UserData": "IyEvYmluL2Jhc2hcbi9l....",
"SecurityGroupIds": [
"sg-01b7bd9742f8feec1"
]
}
}Next, create the template:
$ aws ec2 create-launch-template \
--launch-template-name ubuntu-eks-nodes \
--version-description "Create Ubuntu EKS Template" \
--cli-input-json file://./ubuntu_node_template.jsonFinally, launch a node group using the template.
$ aws eks create-nodegroup --cluster-name eks-cluster \
--nodegroup-name ubuntu-nodes-cli \
--subnets subnet-024699a3e184137fc subnet-06b9aaf79435fe7d8 \
--node-role 'arn:aws:iam::927445640099:role/eksNodeGroup' \
--launch-template name=ubuntu-eks-nodesSee your nodes!
Ensure you are connected to your cluster using kubectl. You
can watch the nodes come online and transition to the ready state with kubectl get nodes -w
Latest Ubuntu EKS AMIs
Ubuntu supports Amazon EKS clusters with the optimized AMIs for the latest EKS Kubernetes versions. You can find the EKS-optimized Ubuntu AMI IDs for a variety of AWS regions on the Ubuntu Cloud Images EKS site.
— Josh Powers (Senior Engineer at Canonical) and Nate Taber (Principal Product Manager for Amazon EKS at Amazon)



